How to prevent CryptoLocker from holding your files to ransom
Posted by: easypccare.co.uk - High Wycombe on 25th October
2013 @ 12.30
Updated by: easypccare.co.uk - High Wycombe on 30th October 2013 @
11.30
*** NEW VERSION RELEASED ***
What is CryptoLocker?
CryptoLocker is a ransomware program that was released around the beginning of September 2013.
This ransomware will encrypt certain files using a mixture of RSA & AES encryption.
When it has finished encrypting your files, it will display a CryptoLocker payment program that prompts you to send a ransom of either
$100 or $300 in order to decrypt the files. This screen will also display a timer stating that you have 96 hours, or 4 days,
to pay the ransom or it will delete your encryption key and you will not have any way to decrypt your files.
This ransom must be paid using MoneyPak vouchers or Bitcoins. Once you send the payment and it is verified, the program will decrypt the files that it encrypted.
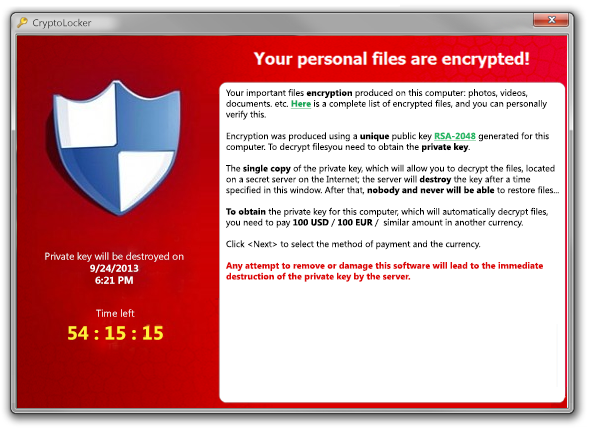
When you first become infected with CryptoLocker, it will save itself as a random named filename to the root of the %AppData% or %LocalAppData% path. The infection will then attempt to find a live Command & Control server by connecting to domains generated by a Domain Generation Algorithm. Some examples of domain names that the DGA will generate are lcxgidtthdjje.org, kdavymybmdrew.biz, dhlfdoukwrhjc.co.uk, and xodeaxjmnxvpv.ru. Once a live C&C server is discovered it will communicate with it and receive a public encryption key that will be used to encrypt your data files. It will then store this key along with other information in values under the registry key under HKEY_CURRENT_USER\Software\CryptoLocker. Unfortunately, the private key that is used to decrypt the infected files is not saved on the computer but rather the Command & Control server.
How to prevent your computer from becoming infected by CryptoLocker
BACKUP YOUR DATA NOW!
The first thing to do is ensure you have a complete back up your files, if you are you using an external drive, once you have backed up your files eject/unplug your external hard drive from the computer. Do not risk the external hard drive getting encrypted.
We would recommend you backup your data to a cloud solution, we can help you with this, give us a call.
FoolishIT LLC was kind enough to create a free utility called CryptoPrevent that automatically adds the suggested Software Restriction Policy Path Rules to your computer. This makes it very easy for anyone using Windows XP SP 2, Windows Vista, Windows Vista Windows 7 and Windows 8 to quickly add the Software Restriction Policies to your computer in order to prevent CryptoLocker and Zbot from being executed in the first place.
PLEASE READ
Please ensure you are running the latest version of CryptoPrevent download from the links below and before applying the protection, click on the Updates Tab.
You should periodically check for and update to the latest version
using the program’s internal update function in the top menu to stay
current with the latest methodology in preventing this (and other)
malware. After an update it is necessary to re-apply the
protection to your system. It is not necessary to undo the
previous protection in place before doing this, or even to uninstall
the app before updating. If you have an older version of
the app before the update functionality was introduced, simply
download and install the latest version, then re-apply protection.
You can download CryptoPrevent form our web
site by
clicking here
You download direct from from FoolishIT own web site by visiting http://www.foolishit.com/download/cryptoprevent/
Once you download the CryptoPrevent you need to
install the program, once installed the program will open with the
following screen:
Click the OK button to continue
Once you have clicked OK you should see the following:
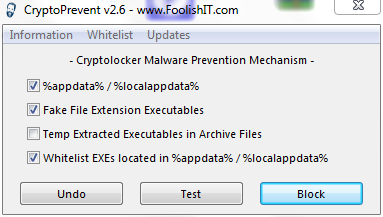
Ensure all 3 options are ticked then click on the Block button
If you click on the Whitelist tab you can add your own safe programs
CryptoPrevent will now apply the polices
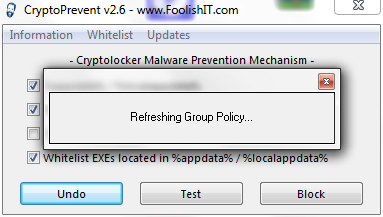
Once the policies have been applied you must RESTART your computer for them to be applied
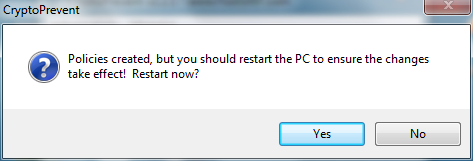
Once you have restarted your computer, run CryptoPrevent and click the Test button
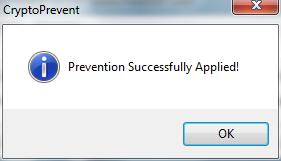
If you have followed the instruction correctly you should receive the message above.
If you are currently a client of ours and would prefer us to install CryptoPrevent for you, we can do this for FREE! We will do this via Remote Assist+. If you are not currently client we can do this for you via Remote Assist+ for £5.00. Clients who use our Virtual Technician Solution need not worry as we have already installed CryptoPrevent.
You can manually edit your Polices, we recommend the option above.
What should you do when you discover your computer is infected with CryptoLocker
When you discover that a computer is infected with CryptoLocker, the first thing you should do is disconnect it from your wireless or wired network. This will prevent it from further encrypting any files. Some people have reported that once the network connection is disconnected, it will display the CryptoLocker screen.
It is not advised that you remove the infection from the %AppData% folder until you decide if you want to pay the ransom. If you do not need to pay the ransom, simply delete the Registry values and files and the program will not load anymore. You can then restore your data via other methods.
It is important to note that the CryptoLocker infection spawns two processes of itself. If you only terminate one process, the other process will automatically launch the second one again. Instead use a program like Process Explorer and right click on the first process and select Kill Tree. This will terminate both at the same time.
Is it possible to decrypt files encrypted by CryptoLocker?
Unfortunately at this time there is no way to retrieve the private key that can be used to decrypt your files. Brute forcing the decryption key is not realistic due to the length of time required to break the key. Also any decryption tools that have been released by various companies will not work with this infection. The only method you have of restoring your files is from a backup or Shadow Volume Copies if have System Restore enabled. If you do not have System Restore enabled on your computer or reliable backups, then you will need to pay the ransom in order to get your files back.
Will paying the ransom actually decrypt your files?
Paying the ransom will start the decryption process of the CryptoLocker infection. When you pay the ransom you will be shown a screen stating that your payment is being verified. Reports from people who have paid this ransom state that this verification process can take 3-4 hours to complete. Once the payment has been verified, the infection will start decrypting your files. Once again, it has been reported that the decryption process can take quite a bit of time.
Be warned, that there have been some reports that the decryption process may give an error stating that it can't decrypt a particular file. At this point we have no information as how to resolve this. Visitors have reported that the infection will continue to decrypt the rest of the files even if it has a problem with certain files.
Contact easypccare.co.uk today and we will assist you with Virus detection, removal and prevention. We will also assist you with backup solutions.
|
Comment Box is loading comments...
|
- Recent Blogs
